The email is also one of the easiest channels for scammers and cybercriminals to exploit. Fake emails are often carefully designed to mimic legitimate messages from trusted brands, banks, or colleagues, making it difficult for an average user to distinguish between real and fraudulent communication.
Phishing attacks commonly rely on deceptive tactics like domain spoofing, character substitution (using look-alike Unicode characters), and misleading sender names. For example, the domain “g00gle.com” may appear almost identical to “google.com” at first glance, but it is a fraudulent attempt to trick users into clicking links or sharing sensitive information. A specialized tool that verifies email headers, sender names, and hidden Unicode variations can immediately highlight suspicious elements.
Professional users, including IT teams, marketers, and corporate employees, can greatly benefit from such advanced checks. By running quick analyses, they reduce the risk of falling victim to scams, protect confidential data, and ensure communication authenticity. With rising online threats, combining user awareness with automated verification tools is the smartest defense against fake emails.
Fake Email Checker:
A fake email checker just inspects an address across several layers to decide if it’s real, disposable, or spoofed.
Quick scan: MX, brand tokens, and Unicode checks — advisory only, not 100% accurate.
First, it parses the address and runs syntax checks and regular expressions to flag obvious fakes. It then performs DNS/MX lookups to see whether the domain actually accepts mail; no MX = likely dead.
The tool often probes SMTP servers (without sending mail) to validate the specific mailbox via SMTP handshake/VRFY/RCPT commands, returning whether the recipient exists. To catch disposable or throwaway services, it compares domains against updated blocklists and known disposable email provider lists.
For spoofing, it examines domain similarity using homograph detection: it normalizes characters and checks for Unicode homographs (e.g., Cyrillic “а” vs Latin “a”) that visually mimic trusted domains. It also checks SPF/DKIM/DMARC records to see if mail from that domain is likely to be forged. Finally, a scoring engine combines signals i.e. syntax, DNS/MX, SMTP response, blacklist match, homograph risk, and authentication records, into a readable verdict (safe, suspicious, fake). The result helps users and systems decide whether to trust, block, or flag the address.
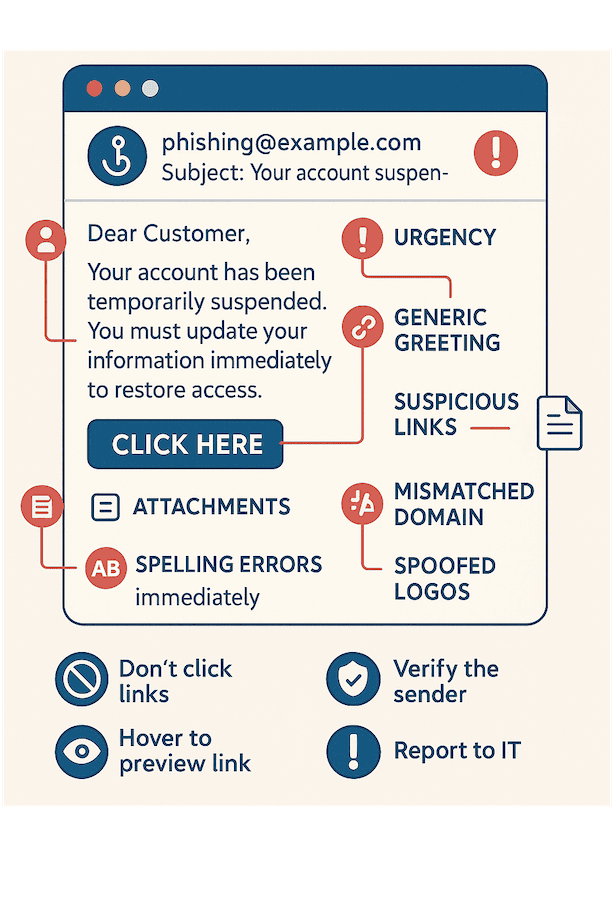
What Does a Fake Email Look Like?
A fake email is written to appear like it’s coming from a trusted source, but the signs reveal its fraudulent nature. These emails often use look-alike domains, such as replacing letters with numbers (e.g., amaz0n.com instead of amazon.com), or use display name tricks where the sender name looks legitimate but the underlying address is suspicious.
They may include urgent messages, such as threats of account closure, or attract you with promises like lottery winnings. Many contain mismatched links, where the visible text looks safe but the real destination leads to malicious websites. Scammers also rely on poor grammar, spelling mistakes, and generic greetings like “Dear Customer” to send mass messages.
How To Spot a Fake Email?
Fake emails are sophisticated, often mimicking trusted organizations. By recognizing some of the signs i.e. domain tricks, hidden Unicode, mismatched links, and emotional manipulation, you can protect your sensitive data and avoid scams.
1. Checking The Unicode Trick
Unicode allows scammers to swap letters with identical-looking characters from other alphabets. For example, the Cyrillic “а” looks identical to the Latin “a.” That means “аpple.com” (with Cyrillic letters) isn’t “apple.com” but a spoofed domain.
Users usually can’t detect this visually, and to uncover hidden characters, copy and paste suspicious domains into a Unicode inspector or plain email checker below. This reveals if letters are from unusual character sets. Many professional email security tools also flag such tricks automatically, but individuals should still be aware and cautious. This tactic remains common in high-level phishing campaigns.
We have a Fake Email Checker where you can input any email ID. It verifies brand authenticity, MX records, and Unicode tricks to instantly show if the email is real or fake.
2. Spotting Domain Imitations
Fraudulent emails often use domains that look deceptively similar to real ones. Attackers register typosquatted versions like “amaz0n.com” instead of “amazon.com” or add extra letters like “gooogle.com.”
Another trick is hiding fake domains behind subdomains, for example, “paypal.secure-login.com,” where the true domain is actually “secure-login.com.”
Always focus on the root domain (just before .com, .org, or similar) and verifying the sender’s actual email domain ensures the message is authentic.
3. Look for Deceptive Display Names
The scammers exploit the fact that email clients often display a “name” alongside the address. They may set the display name as “Amazon Support” while the real address reads [email protected].
Since many users don’t check the underlying address, this trick works well. Criminals often use this in fake order confirmations or refund scams, pushing victims to click links.
The safest approach is to always expand sender details. Hovering over the display name or clicking the “show details” arrow in Gmail or Outlook reveals the real sender address hidden behind the mask.
4. Random Characters in the Address
The fake emails often contain addresses with odd strings of numbers or letters, such as [email protected]. While some users genuinely add numbers, scammers commonly generate such addresses randomly to mass-send spam. Corporate senders usually have structured addresses like [email protected], making odd ones suspicious.
An unusual domain combined with random characters should immediately raise red flags. Be extra alert when these emails also include urgent requests or attachments. Also, a quick search of the sender’s email on Google or LinkedIn may help verify legitimacy.
5. The Reply-To Field
The reply-to field tells your client where responses should be sent. A mismatch here is a strong indicator of fraud. For example, a scam email might appear from [email protected], but its reply-to field redirects to [email protected].
Attackers use this when spoofing official domains they cannot control. In Gmail, Outlook, and most email apps, you can reveal this field by expanding message details or composing a reply. The legal organizations rarely redirect replies outside their domain. If you notice a mismatch, treat the email as suspicious, especially if it contains requests for money, login credentials, or sensitive details.
6. Content Red Flags
Scammers are skilled at manipulating emotions, and their emails include claims like “your account is compromised,” “you’ve won money,” or “an urgent invoice awaits.” These create urgency, excitement, or fear to push hasty action.
They also imitate professional designs with fake logos, layouts, or disclaimers. Always pause and ask: Does this make sense? Would a real company contact you this way? A suspicious message that demands sensitive information or directs you to click without any context. So, checking with the company directly via verified contacts can prevent serious consequences.
📌 Tips
- Watch for lottery or prize claims
- Avoid acting on “immediate action” emails
- Don’t trust logos alone
- Verify claims through official company contacts
7. Urgency and Threats
One of the most common phishing strategies is urgency. These tactics short-circuit rational thinking by activating fear or excitement. Scammers know victims often comply before questioning authenticity. The safest response is to pause. No legitimate company closes accounts or gives prizes through unsolicited emails.
📌 Tips
- Never respond immediately
- Treat threats as red flags
- Verify claims via customer service
- Avoid acting on “immediate action” emails
8. Requests for Sensitive Information
If an email asks for your social security number, credit card details, or passwords, it’s almost certainly fraudulent. The universities, banks, and government agencies primarily emphasize secure channels for such requests.
The best practice is to never share sensitive information via email. If in doubt, call the organization directly using an official phone number. This single can stop some of the most damaging identity theft attacks in their tracks.
9. Grammar, Spelling Errors, and Inconsistencies
While some genuine emails contain typos, poor grammar, and repeated mistakes are frequent in phishing emails. Scammers may lack language proficiency or deliberately use errors to filter out careful readers. Professional companies usually proofread communications and maintain consistent templates.
If an email claiming to be from a well-known brand looks amateurish, it’s a red flag. Just look at these inconsistent fonts, unaligned layouts, and generic greetings like “Dear Customer.” As the organizations with your account details rarely use vague language. Just the simple scrutiny of grammar and formatting can help detect fraud quickly before clicking links or attachments.
10. Mismatched Links
The phishing emails often disguise links to trick recipients. For example, the text may display www.yourbank.com, but hovering reveals a malicious address like www.example.com/login. This “masked link” approach is dangerous. Always hover your cursor over links before clicking to preview the true destination.
On mobile, long-press to reveal the link, and if mismatched, don’t click. Directly type the domain into your browser instead. Professional attackers craft links that look convincing, so it is important. Some security add-ons can automatically warn about suspicious URLs, offering another layer of protection for daily browsing and email checks.
How to Safeguard Yourself From Fake Emails?
Protecting yourself from fake emails requires both understanding and action. You must learn to recognize phishing patterns and combine attention with practical defenses i.e. filters, authentication, breach monitoring, and secure habits, to reduce risk. The proactive measures and ongoing education make it far less likely that an email will succeed against you or your organization.
i) Keep Informed
You should stay updated about new scams and phishing trends. Follow trusted sources like government alerts, security vendors, and industry groups. Always try to share short updates with your team and run training or simulations. If you are aware of current tricks like homograph domains and voice scams, it helps you spot threats faster and report them before damage occurs.
ii) Use Strong Filters
You can set up strong email filters and spam protection to block obvious phishing before it reaches inboxes. You can use advanced services that check sender reputation, URLs, and attachments. Regularly review messages to reduce false positives and combine filtering with endpoint protection so that malicious files cannot run if a message slips through.
iii) Authenticate Your Domain
Make sure you set up SPF, DKIM, and DMARC to stop others from spoofing your domain. You can start monitoring reports, then enforce policies once confident. Include all third-party services that send mail for you, like marketing tools. Regularly review auth reports to catch misconfigurations and impersonation attempts before attackers can abuse them.
iv) Practice Safe Habits
You can use multi-factor authentication and strong, unique passwords stored in a password manager. Never click unexpected links; type important URLs directly into your browser. You should treat attachments cautiously and confirm unusual requests by phone. You must promote a no-blame reporting culture so staff report suspicious emails immediately, helping the whole organization respond faster.
Frequently Asked Questions:
Unicode or homoglyph detection checks for non-standard characters that look like normal letters, such as Cyrillic “а” for Latin “a”. Attackers use these to register deceptive domains. The tool flags unusual characters or Punycode. If detected, avoid clicking links and verify the sender manually through trusted channels before taking action.
MX checks confirm which mail servers accept email for a domain. If a domain lacks MX records, mail delivery may be unreliable, or the domain could be misconfigured or fake. Our checker verifies MX on the root domain to spot subdomain tricks.
If the checker flags an email, don’t click links or open attachments. Verify sender identity using known contacts or the company’s official website and phone numbers. You can forward the message to your IT or security team and report phishing to the email provider.

